Understanding AI Security Readiness
The Strategic Challenge Facing Security Teams
Security teams recognize Shadow AI as a critical threat, but lack clarity on where to begin when employees are already using multiple unsanctioned AI tools.
The problem isn't just theoretical. Organizations with unmanaged Shadow AI exposure experience an average of $670,000 more per data breach compared to those with mature AI governance (IBM Cost of a Data Breach 2025).
Unlike traditional Shadow IT, AI tools actively analyze and potentially store your data for model training. Employees naturally paste entire documents, not just snippets. One employee can expose thousands of records in seconds—and you'll never know it happened.
This assessment helps you prioritize: Rather than building comprehensive frameworks without addressing critical gaps first, discover where your organization stands and get clarity on what to tackle next.
AI Security Readiness Assessment Preview
See What You'll Experience
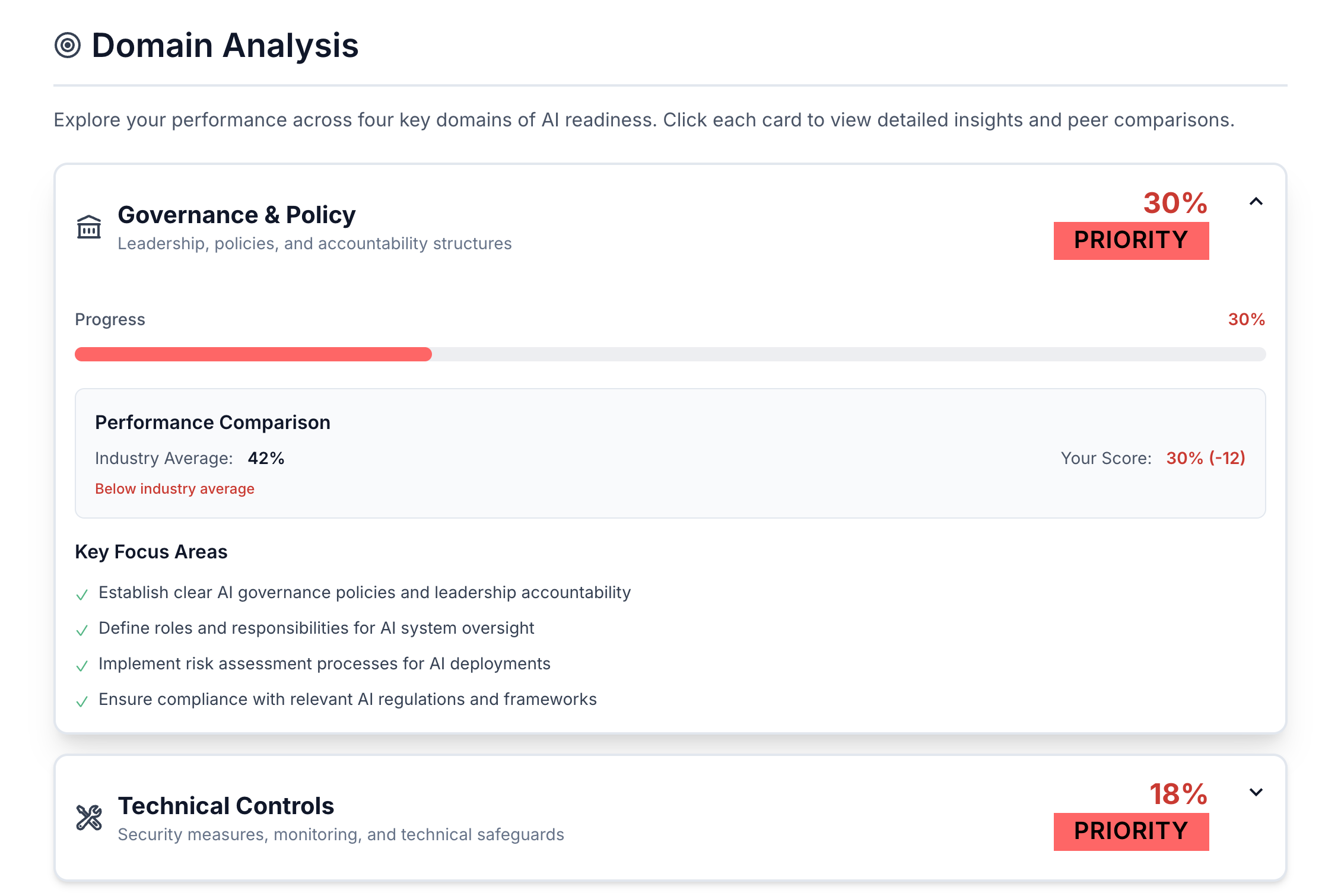
This 5-minute assessment evaluates your organization's maturity across four critical domains, providing a personalized roadmap with immediate quick wins and strategic initiatives.
Assessment Domains:
No vendor pitch or sales call required. Results are completely confidential.
Start Your AssessmentWhat You'll Receive
Comprehensive insights to strengthen your AI security readiness
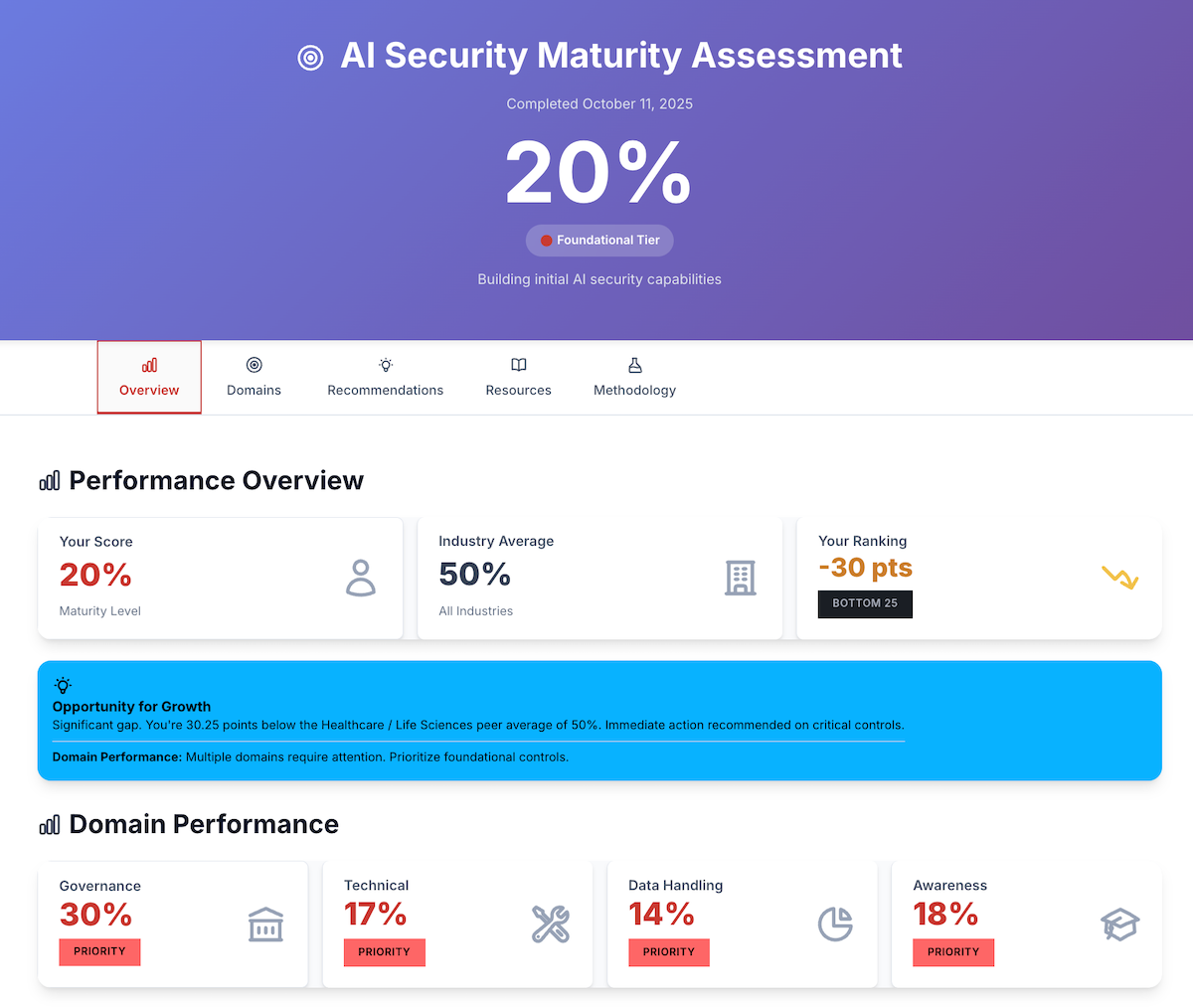
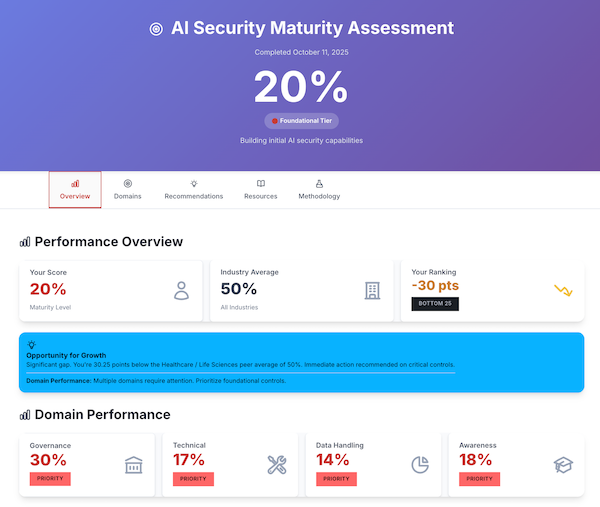
Maturity Score
0-100% benchmark across all four domains
Tier Classification
Foundational, Developing, or Adaptive tier
Priority Roadmap
Strategic plan identifying critical gaps first
Quick Wins
Immediate actions for 2-4 week implementation
Benchmarks
Compare your posture to industry standards
Why AI Security Readiness Matters
The risk isn't theoretical. When employees paste customer data, source code, or financial records into public AI tools, you've effectively handed your crown jewels to a third party with unknown security practices.
Traditional Shadow IT involved unauthorized software or cloud services. Shadow AI adds three critical dimensions:
- Active data analysis: These tools process and potentially store your data for model training
- Conversational interfaces: Employees naturally paste entire documents, not just snippets
- Immediate blast radius: One employee can expose thousands of records in seconds
AI security readiness requires a strategic approach: policy first, discovery second, controls third. Organizations that check their readiness before implementing controls see measurable risk reduction within the first 90 days.
See how you score against other organizations in your industry
Assess Your AI Security ReadinessHave Questions?
Learn more about AI security readiness, Shadow AI detection, implementing controls, and measuring your organization's maturity in our comprehensive FAQ.
View FAQ